There is no time to waste. Here is our 13-point checklist intended for industrial and critical infrastructure operators.
See the full NIS2 Directive
1. Is my company subject to NIS2?
Any large or medium-size EU-based company involved in the following industries is subject. Companies that may be operated outside the EU but provide these services/products might be subject as well.
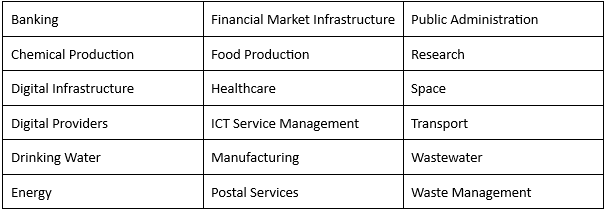
Usually depending on size, enterprises involved in the above industries are considered by NIS2 to be “Essential Entities” or “Important Entities” and subject to the Directive. See our NIS2 whitepaper for a deeper discussion.
Network segmentation is a vital security practice that cordons off one network from another, for example, to separate the OT network from the IT network, or one critical manufacturing network from another, or one part of the factory floor from another, etc.
We segment networks for the same reason that we install fire doors in buildings or watertight doors in submarines: If a disaster happens in one area (fire, flood), we can contain the problem there and prevent it from spreading. Network segmentation acts to restrict a cyberattack to one section of the network, preventing the damage from spreading.
While NIS2 does not mention it directly, network segmentation is considered a best cybersecurity practice and a highly desirable one for safeguarding operations. In fact, it is included in the widely established IEC 62443 standard that cybersecurity and risk management solutions rely on, so it’s important to do it.
Radiflow advises on effective segmentation strategies. Some of our technology partners offer excellent solutions for implementation segmentation.
Over decades, OT devices and other assets are added, removed, and modified. What’s out there? What is it doing? With what other devices/controllers/applications/systems is it talking? Who is directing its operation? To assure secure operations, you have to know the answers to these questions.
Radiflow automatically finds and maps all assets and registers other vital information about them in a sharable asset inventory. Unobtrusively, Radiflow passively monitors all communications on the network to find and monitor assets. Employing safe, targeted methods, Radiflow can communicate with OT assets using their native protocols.
OT supply chains are lengthening. Machines and complex devices are often constructed from a variety of assets manufactured by an assortment of vendors. Systems like navigation and propulsion rely on outside operators to function. If any of the hardware, firmware, software, or communication along the supply chain is vulnerable to attack, then the operation can be at risk.
Radiflow CIARA uses millions of data points from the ICS network to discover supply-chain vulnerabilities and accurately assess their risk. Operators can quantify the effectiveness of various mitigation measures to maximize their cyber resilience while reducing risk.
Organizations may be in different stages of cyber-development. Some already have well-funded SOCs equipped with and arsenal of security solutions while others are just getting started on their cyber journey and are looking for cost-effective, easy-to-implement solutions. Some have large security budgets while others can only dream. Some want to take on the cyber challenge in-house, while others prefer to outsource.
Radiflow offers effective cyber solutions that enable organizations to safeguard their operations. Radiflow and several of its partners also offer managed security services. We are in a unique position to advise you on the best way forward for your organization.
NIS2 does not specify cybersecurity standards, but calls for adoption of accepted standards like IEC 62443 and/or the NIST Cyber Security Framework. These standards constitute the basis for Radiflow solutions. Radiflow assesses the gaps between current practices and accepted standards, evaluating security controls and their effectiveness. It also evaluates mitigation measures for maximum effect on risk while optimizing the security budget.
Vulnerability management is a continuous, proactive, and automated process that keeps the ICS network safe from cyberattacks and data breaches. Radiflow solutions help OT operators achieve the five critical aspects of the Vulnerability Management Lifecycle:
NIS2 places demanding requirements regarding incident reporting. OT organizations must report incidents to their national Computer Security Incident Response Team (CSIRT) within 24 hours of becoming aware of a significant incident. A final report is required no later than one month after the initial Incident notification.
Radiflow automatically detects incidents and collects forensic and other information necessary for prompt and proper incident reporting.
Article 21 of the NIS2 Directive sets out clear cybersecurity measures “to protect network and information systems” that focus on ensuring business continuity through “backup management and disaster recovery.” Organizations must plan for how they intend to ensure business continuity in the case of major cyber incidents. This plan should include considerations about system recovery, emergency procedures, and setting up a crisis response team.
Through expertise acquired over decades of safeguarding operational technology, Radiflow is able to advise organizations on suitable best practices for compliance with NIS2 while ensuring their business continuity.
NIS2 greatly expands the requirements of risk assessment to a comprehensive, ongoing risk management program. Data-driven CIARA helps security teams proactively manage cyber risk and build resilient operations while complying with risk management directives and regulations like NIS2, IEC 62443, and NIST CSF, and industry best practices. CIARA automatically discovers and learns key risk indicators and accurately evaluates security posture and risk per site and overall. It determines how to direct the OT security budget to maximize the effectiveness of threat-mitigation measures. CIARA delivers prompt, automatic, accurate, and compliant risk assessments, slashing assessment and audit time.
NIS2 requires Member States to ensure that management bodies approve cybersecurity risk-management measures, oversee their implementation, and participate in specialized cybersecurity training. Managers may be held personally liable for violations. Cybersecurity has become an issue that will make a direct impact on the corporate governance.
Radiflow conducts cybersecurity training for senior management, helping them to understand the requirements of NIS2, their roles, and potential liabilities.
Under NIS2, cyber training is not only relevant for senior management but for all employees of the company and even service providers. Radiflow provides comprehensive, recurring training on cybersecurity and awareness, including best practices, data handling, and compliance obligations, pertinent to roles within the company.
Cybersecurity is a moving target. The threat landscape is always advancing as are networks and devices. New vulnerabilities are discovered every day while companies suffer attacks around the clock.
Radiflow keeps its customers protected against old and new threats. Constantly fortified with the latest threat intelligence and industry best practices, our solutions identify and quantify the gaps between full compliance and current security controls.
OT organizations rely on Radiflow to aid their journey toward NIS2 compliance.
Want to learn more about NIS 2 compliance and how Radiflow can help? Contact us for more information

For more information, download our whitepaper

Proactive Risk Monitoring: The Key to OT-SOC Efficiency & Cyber Resilience

Why Being a Niche Player Can Be Your Strategic Advantage: The Radiflow Case

Bug or Feature? The “Backdoor” in CONTEC CMS8000 Patient Monitor