The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is an American cybersecurity directive comprising guidelines and best practices for ensuring adequate cybersecurity and risk management for critical infrastructure. Initiated in 2013, the directive introduced efforts for sharing cybersecurity threat information and created a set of successful approaches for reducing risks.
NIST CSF is an evolving approach to cybersecurity. Since its initial release, it has undergone several updates and revisions to address emerging threats, technological advancements, and best practices. NIST published a formal update to the CSF in 2018, introducing guidance on self-assessments, supply chain risk management, interaction with supply-chain stakeholders, and developing a process for disclosing vulnerabilities.
NIST CSF was initially developed to protect America’s critical infrastructure – the assets, systems, and functions deemed vital to the country. Presidential Policy Directive 21: Critical Infrastructure Security and Resilience, defines the 16 critical infrastructure sectors:
Today, NIST CSF is not limited to US critical infrastructure. The popularity of the Framework has expanded well beyond the United States. It has been translated into many languages and is used by several governments and a wide range of businesses and organizations. The Framework is considered a cornerstone in cybersecurity risk management and a vital tool in threat prevention.
In establishing CSF, NIST used as its design criteria:
The NIST CSF framework comprise three main components:
The Core is really the heart of the CSF. It outlines a set of cybersecurity activities and outcomes across five key functions:
Each of the functions is further broken down into categories that cover topics across cyber, physical, and personnel with an emphasis on business outcomes. The categories are further broken down into 108 subcategories.
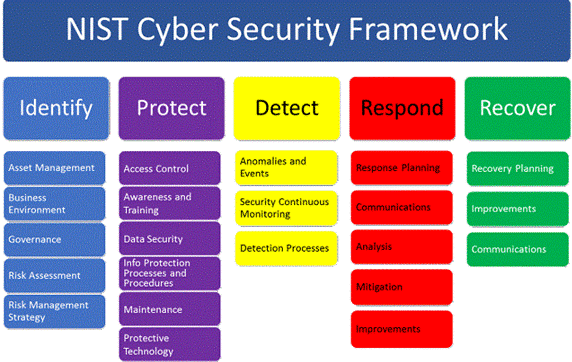
Core Functions and Categories
NIST CSF is not intended as a one-size-fits-all framework. Each organization decides to which functions, categories, and subcategories it wishes to comply.
Ranging from 1-4, Implementation Tiers do not refer to maturity levels. Instead, they show how well cybersecurity risk decisions are integrated into broader risk decisions and the degree to which the organization shares and receives cybersecurity information from external parties. Organizations fall into one of four tiers that represent the degree to which they have implemented NIST controls:
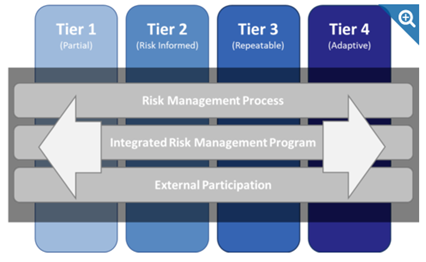
Implementation Tiers
Tiers can be:
Every organization is different. Profiles indicate how the Cybersecurity Framework may best serve the organization. There is no ‘right’ or ‘wrong’ way. It is up to the organization to adapt the framework to its needs. The organization should map cybersecurity requirements, mission objectives, and operating methodologies, along with current practices against the categories and subcategories of the Core (see above) to create a Current State Profile. Requirements and objectives can be compared with the current operating state of the organization to gain an understanding of the gaps and the associated costs for closing them.
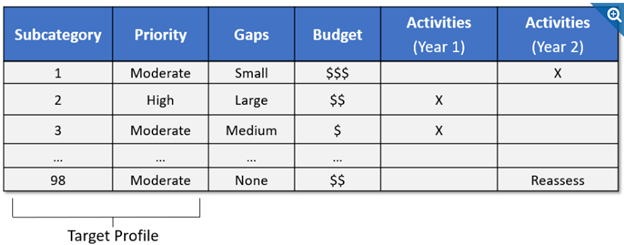
Gap and Budget Analysis with Respect to the Organization’s Profile
Certain US-based organizations are required to comply with the NIST CSF. However, for most organizations, compliance is optional. Many choose to comply to assure themselves and their customers that their systems, network, and data are as safe as possible from a cybersecurity incident.
In addition, compliance with NIST CSF can ease the way to compliance with other security frameworks such as the Payment Card Industry Data Security Standard (PCI DSS) and the Sarbanes-Oxley Act (SOX). NIST CSF also governs compliance with the Federal Information Processing Standard Publication 200 (FIPS 200), mandatory for government-affiliated entities.
The NIST CSF directive is flexible and can be customized to fit the unique needs and requirements of any particular region or industry.
NIST CSF has rapidly become one of the most widely employed cybersecurity frameworks in the USA, but that’s not to imply that it’s easy to implement – it isn’t.
Compliance with NIST CSF enhances overall cybersecurity posture by providing a comprehensive framework for risk management, and fosters consistency and alignment with industry best practices. By following the directive, industrial and critical infrastructure organizations are able to enhance trust and confidence among customers, partners, and stakeholders, safeguarding sensitive data and reducing the risk of breaches.
Risk management – adjusting the threat mitigation controls mix toward reducing the impact of materialized cyber-threats, accounting for the damages incurred by each potential threat to each and every business unit, weighted for probability each threat materializing – constitutes a major component of the NIST CSF directive.
CIARA, Radiflow’s Risk Assessment and Management platform, helps OT organizations comply with multiple standards, including NIST CSF. It provides clear insights for optimizing OT cyber-security-based threat prioritization and maximizing the effectiveness and ROI of the network security system.
CIARA serves as a significant compliance enabler for NIST CSF, covering all five functions and 13 of the categories defined in the NIST CSF Core. These are described in the table below. Note: the category codes in parentheses reflect the formal way that the NIST Framework refers to them.
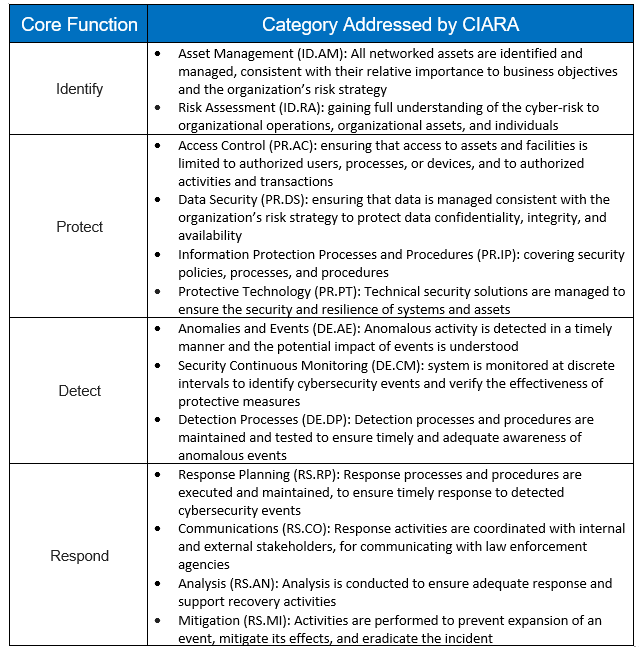
CIARA clearly displays each individual security control (subcategory) with a graphic summary of the percentage of completion for each. Using CIARA, organizations gain a quick and complete understanding of where they stand in compliance vis-à-vis their Profile and their chosen Implementation Tier.
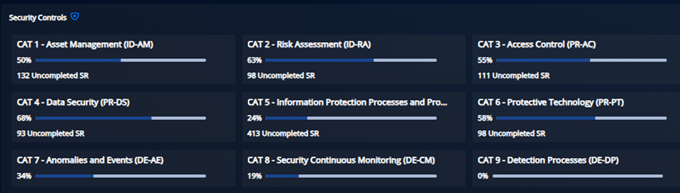
In one neat graphic, CIARA summarizes the overall implementation status. At a glance, the organization knows how well it is complying with the scope of the NIST CSF.
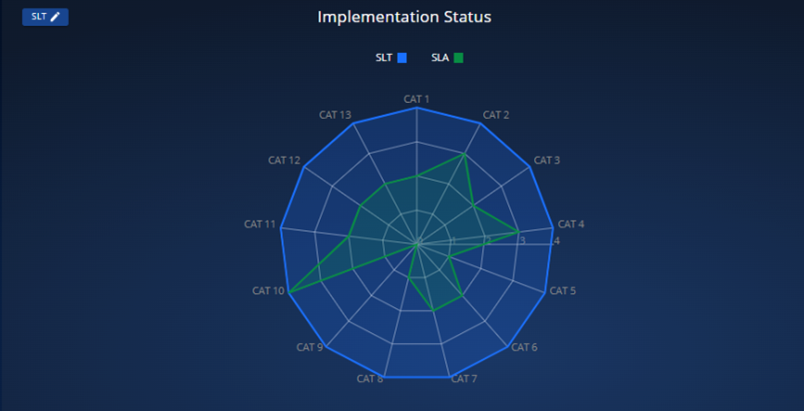
CIARA also graphically displays the organization’s compliance improvements over time per function and category. Users can readily see their rate of improvement by quarter or other time period.
CIARA Risk Assessment and Management is a vital tool in the arsenal of the OT organization that wants/needs to comply with the NIST CSF. CIARA analyzes, tracks, and simplifies the compliance process, helping organizations to continuously improve their security posture and compliance level.
Contact Radiflow to see a demo of CIARA and what it can do for your organization.
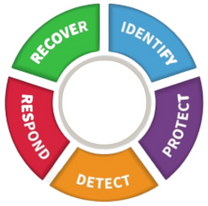
The NIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks

Renewable Energy Cybersecurity Wake‑Up Call: What Poland’s 29 December 2025 Incident Should Change

Hacktivists Are Hijacking Exposed ICS Devices — Here’s What Every Operator Must Know

The JLR Cyber Incident: A Wake-Up Call for Manufacturing Resilience