
Synopsis:
Cyber-mining malware enables crypto-currency miners to use some of the processing power of an infected computer for mining cyber-currency.
This case study describes the process of detecting and eliminating the malware on SCADA servers operated by a water utility. The process utilized Radiflow’s iSID for analyzing network traffic captured by Radiflow Smart Probes.
Once iSID detected abnormal activity it was able to indicate the port and destination IP address used for the attack, which were used to update the utility’s anti-virus and firewall rules and prevent the recurrence of such attacks.
The Detection Process
In the case described in this paper, the network attacked by crypto-mining malware belonged to a water utility. As it was used primarily for serving a cloud-based OT analytics system and for remote maintenance, the water utility’s network needed to be connected to the internet.
The process of detecting and eliminating malware on the utility’s SCADA network started with connecting iSID to the network. iSID is Radiflow’s multi-engine platform for monitoring SCADA networks. It includes six engines for detecting known vulnerabilities, topology anomalies and asset management.
On January 21st, 2018 , Radiflow’s iSID Intrusion Detection System was connected to the network, using a Radiflow Smart-Probe. The Smart-Probe enables deploying iSID at a central location and sending a mirrored network traffic stream through using a secure IP tunnel, through diodes, to iSID.
Later that day, the first events began to come in from iSID’s engines:
Once the initial events were reported, Radiflow’s research team began to further analyze the detailed network information.
Looking up the destination IP address (using Virus Total) did not lead to any malicious site. While (securely) visiting this IP address, we found that it belonged to a “MinerCircle Monero Pool” (http://xmr-4.minercircle.com).
A visit to Monero’s mining site revealed that there are several other mining pools:
Monero Mining Pools
One of the most useful features of iSID, as pertains to this case, is the ability to quickly add new activity signatures and backwards-scan them. We loaded iSID with two signatures:
Based on activity signatures, iSID confirmed several IP addresses related to miners:
Traffic volume per IP address
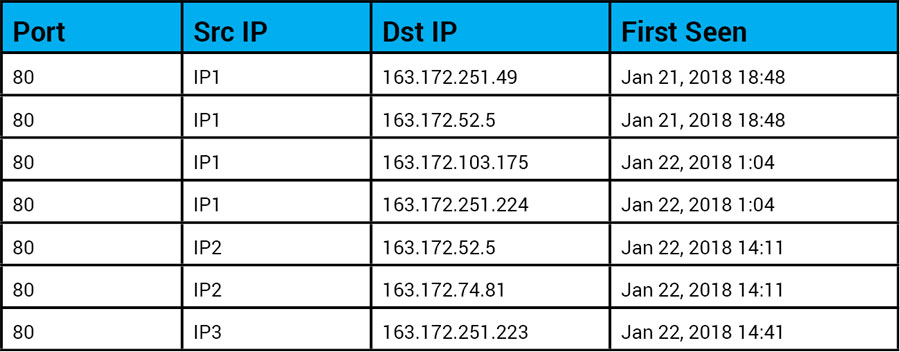
Samples of communication time and first time seen for each IP address. (source IP addresses were masked to protect the customer information.)
Once detected by Radiflow, the water utility operator was informed about the miner malware and about the infected servers.
In the course of devising a recovery scheme for the utility, we deliberated whether it would be possible to update the anti-virus software on the infected servers.
Eventually, the mitigation plan included updating the AV on some servers where it was possible, as well as tightening the firewall configuration. The updated AV detected the CoinMiner malware, as expected.
During the recovery process, iSID continued to monitor the network and collect forensics data, including pcap files and payloads sent during the malicious communications.
Effects on the SCADA Network
CoinMiners present several risks to SCADA networks. The mining procedure is extremely CPU-intensive, leaving much less processing power for the operational software. This caused the operational monitoring software to react slowly, akin to using degraded hardware.
Thus, a server infected by a miner malware creates a problematic situation, since SCADA vendors enforce specific hardware requirements for their software, and provide assurances only for those hardware specifications (but not for degraded hardware.)
In this case the hardware platform indeed met the SCADA vendor’s hardware requirements; however the miner malware had degraded the actual resources left for the operational SCADA software, increasing the risk for operational faults.
Another effect is the increased amount of traffic sent over the internet. In this case, about 40% of the traffic was classified as related to mining operations – causing overall bandwidth consumption to increase by 60% (!) For limited-bandwidth networks, this poses the risk of creating a bottleneck in the facility’s operational data-streams.
Conclusion: best practices in protecting SCADA servers against crypto-mining (and other) malware

OT Cyber Resilience Webinar Series

Renewable Energy Cybersecurity Wake‑Up Call: What Poland’s 29 December 2025 Incident Should Change

Hacktivists Are Hijacking Exposed ICS Devices — Here’s What Every Operator Must Know