If you’ve found this article interesting, please visit and follow Radiflow on LinkedIn, where you’ll find a wealth of exclusive content.
The News
Colonial pipeline is one of the largest fuel pipeline operators in the US, and is responsible for delivering fuel
from Texas to the East Coast.
On May 7, 2021 multiple news outlets reported that a criminal hacker group known as Darkside, which emerged in August 2020, had deployed ransomware in Colonial Pipeline’s IT network. There have been no published indications that the malware made its way into Colonial’s OT network.
In response to the attack targeting its facilities the company stated, “we proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations, and affected some of our IT systems”. As of today, a week after the attack, pipeline operations have only partially resumed. Some sources claim that Colonial had paid ransom to the hackers.
(Read the CISA advisory for the Darkside attack, based on the MITRE ATT&CK framework.)
[inject id=’code-47fd23f73a9caecab1e206306adae7f9′]
Behind the News
- Attacks of this type usually start with phishing or spear-phishing, using a malicious payload embedded in seemingly benign emails to employees. The attackers can then control the malware and instruct it to seek additional access credentials, while at the same time stealing and encrypting the victim’s IT/OT assets.
- In our assessment, the decision to halt pipeline operations and disconnect OT networks was made based on internal risk assessment taking into account multiple factors, such as
- The crisis management process including possible negotiations with the hackers
- Incident response process, which according to publications is led by Mandiant
- Internal knowledge of OT network connectivity and vulnerabilities which may had made it possible for the malware to propagate further.
- The Darkside group has in the past breached and infected networks operated by enterprise-scale companies, including companies in the manufacturing sector, mainly for financial gain, basically operating in a “ransomware-as-a-service” model.
- According to most threat intelligence companies the Darkside group is based in Russia and has been known to actively exploit initial access vulnerabilities: remote access software exploits, purchasing access credentials from underground forums and such. Over the past few days, US government officials, while not explicitly claiming that the Russian government was involved in the attack, have hinted that the Russian government did know about Darkside and similar attack groups but failed to take action to stop them.
What could Colonial Pipeline do to prevent similar attacks?
There’s no single panacea for preventing ransomware and other malware, nor is it a quick fix.
Nevertheless, the following guidelines can help ensure the security of OT networks:
- First, the basic guidelines for OT network protection need to be implemented: segmentation between IT & OT networks; hardening access and user management procedures such as multi-factor authentication; continuous monitoring of network activity to detect signals malicious activity and abnormal network activity, etc.
- In many cases HMI & SCADA servers reside on Windows™ machines that have either reached their end of life or have been left unpatched for a long time. This would make it very easy for attackers to take over and gain malicious control over the HMI & SCADA servers.
- Also in the case of the fuel distribution/pipeline industry: the network topologies used by companies in the field often support easy and smooth remote access to unmanned operational facilities, which aren’t always secured according to best practices. Remote access to unmanned facilities needs to be hardened and limited to the specific devices and operations specified in each maintenance session’s work order.
- Only a complete risk assessment, based on empirical threat intelligence and simulation of all threats and corresponding protection measures, could determine the optimal risk mitigation measures that could ensure protection against ransomware and other malware.
Radiflow’s multi-tier OT security solution provides threat detection, visibility into network & device properties and risk assessment and management services, to ensure maximum automation network security while optimizing expenditure. We invite you to experience a demonstration of Radiflow’s solutions and to learn how Radiflow can help secure your network.
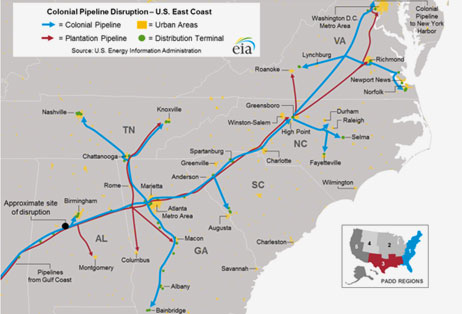
The Colonial Pipeline is the largest fuel pipeline operation in the US. (Image : U.S. Energy Information Administration)


