On August 20, 2022, SecNews.gr announced that Greek Natural Gas Supplier DESFA had a day earlier suffered a cyber attack on part of its IT infrastructure: “Cyber attack on DESFA by foreign hackers, through Ragnar Locker ransomware and data interception took place on August 19, 2022 at 18:42. Hackers infected the National Gas System Operator’s systems with ransomware and managed to steal sensitive employee and customer data and information.”
Sometime later, leaked DESFA files showed up on the dark web:
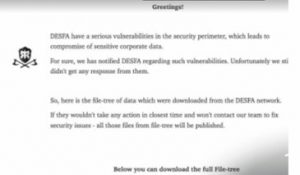
Apparently, the hacker/blackmailers essentially have been stealing files from DESFA for a long time, and have threatened to share these files if the ransom is not paid.
At current, according to DataBreachToday, 361 gigabytes of what appears to be confidential data belonging to Greek national natural gas pipeline operator DESFA, after DESFA refused to negotiate with the hackers.
Among the leaked documents, some of which were posted on SecNews are engineering designs and budget and revenue documents, in addition to several files that appear to be future budget and past revenue spreadsheets; copies of non-disclosure agreements with customers and partners; engineering designs and their backups in a directory format (the authenticity of the data could not be immediately verified.) It is not clear the types and the extent of stolen personal data (PII).
According to DESFA, all industrial operations (OT) related to the Greek national natural gas system kept operating as usual and the damage was only to the IT of DESFA. “The management of the NNGS continues to operate smoothly and DESFA continues to supply natural gas to all entry and exit points of the country safely and adequately”
DESFA’s ability to maintain continuity of its OT operations was probably achieved thanks to the implementation of proper security controls between the breached IT environment and OT the networks which continued to function.
Critical infrastructure utilities should, accordingly, take action in two parallel paths:

DESFA’s ability to maintain continuity of its OT operations was probably achieved thanks to the implementation of proper security controls between the breached IT environment and OT the networks which continued to function.

Proactive Risk Monitoring: The Key to OT-SOC Efficiency & Cyber Resilience

Why Being a Niche Player Can Be Your Strategic Advantage: The Radiflow Case

Bug or Feature? The “Backdoor” in CONTEC CMS8000 Patient Monitor